Problem Description: When you run win_ping from Ansible tower against Windows server and use domain credentials you get “Kerberos auth failure for principal” error.
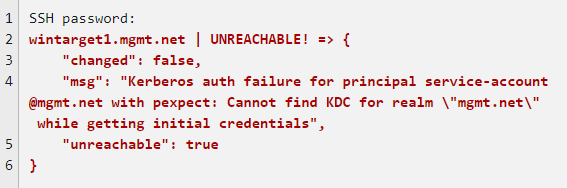
There could be multiple reasons behind the issue, please see the solution section for all possible cause and solutions.
Solution:
- Make sure you have installed Kerberos on the Ansible machine and krb5.conf file is configured. Please note it is krb5.conf and not krb.conf. The file is /etc/krb5.conf
Please make sure the domain name you enter in config file is capitalized.
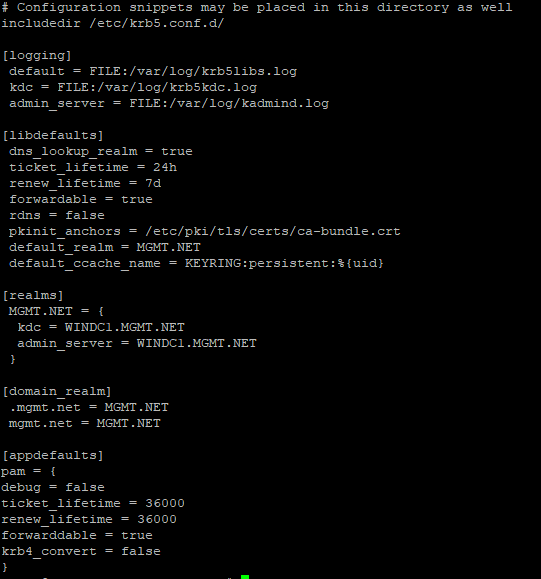
2. Please make sure you are using FQDN of the target machine of windows server and not IP address of
3. In the credentials section, the domain account that you are using should be in the format of account@DOMIAN.COM
As we have entered domain name in CAPITAL letters in krb5.conf file, in the credentials section the domain name must be entered in CAPITAL letters.

Team,
I need help with ansible to windows server 2012.
I get below error
orbdev03.orbit8.com | UNREACHABLE! => {
“changed”: false,
“msg”: “Kerberos auth failure for principal opc@ORBIT8.COM with subprocess: kinit: Improper format of Kerberos configuration file while initializing Kerberos 5 library”,
“unreachable”: true
}
Please let me know if you need any more information
Dear Suresh,
Apologize for delayed response, I was occupied with some other work.
Can you please share configuration of /etc/krb5.conf and /etc/krb.conf
You may remove actual domain name from file when you share the file config.
Also please make sure domain name and realm name and domain controller name are in CAPS
Am also getting a similar error when trying to connect to a Windows client.
Kerberos auth failure for principal abc@XYZ.COM with pexpect: no such file or directory.
Python module pexpect is already installed on the ansible server. Do we need to install anything else ?? Does this module need to be installed this in the Windows client node as well ??
Please reply at your earliest convenience.
Please make sure you have setup WinRM Listener on Windows-
https://docs.ansible.com/ansible/latest/user_guide/windows_setup.html
Also please update inventory to ignore SSL certificate validation-
https://www.servertrouble.com/max-retries-exceeded-with-url-wsman/
From your error it appears Ansible is unable to locate /etc/krb5.conf file. If there is no such file then please manually create it as mentioned in article here.
Hi Pankaj,
I am getting similar kind of error. I am trying to clear the issue from past 3 days, but invain. Can you please help me.
{
“unreachable”: true,
“msg”: “Kerberos auth failure for principal nvenkat-admin@SERCOTEST.COM with subprocess: kinit: Cannot find KDC for realm \”SERCOTEST.COM\” while getting initial credentials”,
“changed”: false
}
Thanks,
Nagaraju
From the error it seems you did not install Kerberos on the Ansible machine.
if you are using RedHat Linux then-
yum install krb5-workstation
yum install krb5-devel
yum install krb5-libs
Also can you post the config of krb5.conf file?
Hi Pankaj,
Thanks for the reply. I appreciate your quick turnaround. Please find the contents of the krb5.conf below.
includedir /etc/krb5.conf.d/
[logging]
default = FILE:/var/log/krb5libs.log
kdc = FILE:/var/log/krb5kdc.log
admin_server = FILE:/var/log/kadmind.log
[libdefaults]
dns_lookup_realm = true
ticket_lifetime = 24h
renew_lifetime = 7d
forwardable = true
rdns = false
default_realm = SERCOTEST.COM
[realms]
XXXXXTEST.COM = {
kdc = SCOAZEU1QADS101.XXXXTEST.COM
admin_server = SCOAZEU1QADS101.XXXXTEST.COM
default_domain = XXXXTEST.COM
kpassword_server = SCOAZEU1QADS101.XXXXTEST.COM
}
# EXAMPLE.COM = {
# kdc = kerberos.example.com
# admin_server = kerberos.example.com
# }
[domain_realm]
# .example.com = EXAMPLE.COM
# example.com = EXAMPLE.COM
.xxxxxtest.com = XXXXXTEST.COM
xxxxtest.com = XXXXXTEST.COM
Actually, kerberos is working perfectly on the linux machine, but it is not working on the Ansible AWX.
[dscadmin@sra5tm-anawx etc]$ ansible -m win_ping windows
sra5tm-awvd-6.XXXTEST.COM | SUCCESS => {
“changed”: false,
“ping”: “pong”
}
sra5tm-awvd-7.XXXXTEST.COM | SUCCESS => {
“changed”: false,
“ping”: “pong”
In the inventories setting of AWX, I have mentioned the following:
—
ansible_port: 5985
ansible_connection: winrm
ansible_winrm_transport: kerberos
In the credentials of AWX, I have mentioned my username as nvenkat-admin@XXXXTEST.COM and mentioned the password too.
Please add below mentioned lines to [libdefaults] section
pkinit_anchors = FILE:/etc/pki/tls/certs/ca-bundle.crt
default_ccache_name = KEYRING:persistent:%{uid}
Also to the inventory please add
ansible_winrm_server_cert_validation: ignore
If possible use Windows local credentials to see if it works, just to make sure there is no other issue.
Hello,
We get the same error for some Users in our AD. But not for all Users.
My User was created in 2019 and with this the deployment is working.
But my colleagus accounts were reated in 2013, and 2015 and with it it does not Work. With newly created users it works.
Do you know something what can be the difference here?
Can you check the UPN for the users getting errors? I suspect the UPN for users are not properly setup and hence Kerberos authentication is failing for them when you try Kerberos from Ansible.
Hello,
The UPN looks for every user the following way:
user@domain.hu
Also the pre windows log on name:
doman\user looks identical.
We checked all attributes for the Users and there are only some minor diferences. ANd on User has identical attributes with my User. We also checked the Network traffick with wireshark during the Kerberos authentication.
Maybe we will give this up….